When you buy stuff online, most websites will let you view the status of your order. This page usually includes your address, phone number, and details of what you ordered. Typically, the order status page is shielded from public view either by a login page or complex encoding. Neither appeared to be in use by a major Honda parts website, which has been inadvertently leaving personal user information, including phone numbers and credit card information, open for viewing by anyone on the internet.
The Autopian was tipped off by a Honda customer who had recently ordered a Motocompacto. They visited the Honda Dreamshop parts site to determine the status of their order, a wise move after many orders were canceled early on. Checking an order is done by entering two out of three of the following on Dreamshop’s Find My Order page: order number, email address, or billing zipcode. Once submitted, the user is taken to a URL for their order ID, where they can see all the relevant information.
Sounds secure? Not in the slightest. A wily ten-year-old could crack this one wide open. Here are a few orders we were able to source almost instantly (we’ve blurred all the personal information because we’re not jerks).
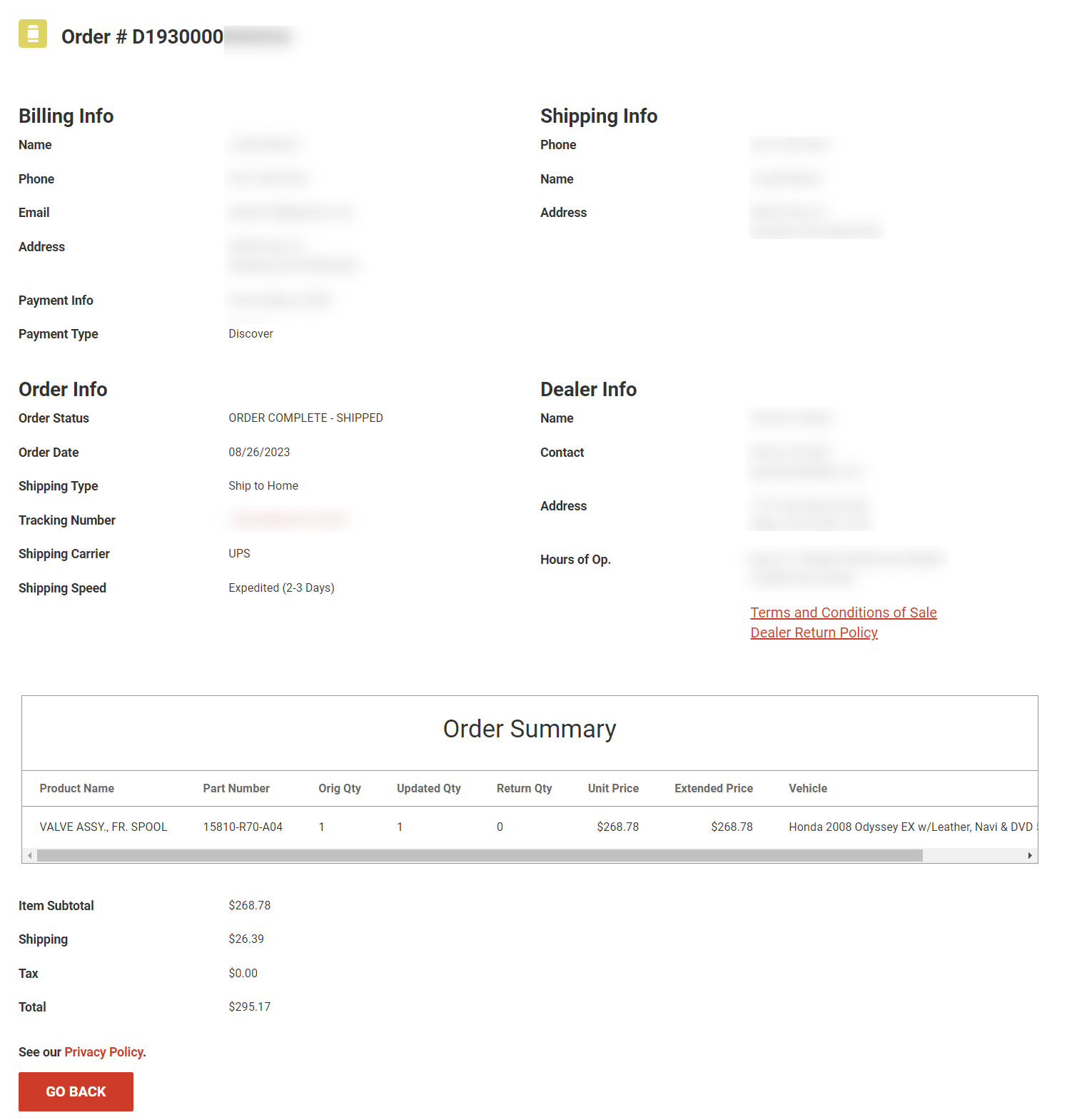

The problem is that there was no obvious authentication used on the website. All one had to do was swap out the order ID in the URL for another number, and boom! It’s possible to see all the details of other customers who have bought parts on the Dreamshop site.
The order page contains a customer’s name, billing address, shipping address, phone number, and email address. It also includes a full list of parts ordered and details of the dealership that took the order. Finally, both the credit card type and last four digits of the user’s credit card are also openly visible.
Upon verifying, The Autopian immediately notified Honda of the issue and held publication of this story until it was verified to be resolved or at least no longer easily discovered. Screenshots shown in this article have been redacted to maintain the privacy of affected individuals. We notified Honda late on Sunday night, and the company replied approximately 18 hours later saying it had removed the visible orders. The pages now read: “This page is currently under maintenance. Apologies for the inconvenience. Please check your email for order details.” As for a statement from Honda, we will update this story as soon as the company has one for us.
Update (Nov 13, 2023 18:57 ET): Here’s a statement from Honda:
American Honda is aware of a potential vulnerability in the Honda Dream Shop website that may have exposed limited customer information to unauthorized users. We take the security and privacy of our customers very seriously and took quick action to temporarily disable one function on the website – the order search page – as a precautionary measure. We are working diligently to investigate and resolve the issue as soon as possible, but the rest of the website is functioning normally, including the ability to securely order a Motocompacto. We apologize for any inconvenience this may cause to our customers and we appreciate their patience and understanding. We will provide further updates as we continue our investigation.
The common sense expectation of most consumers is that any page that shows personal information needs to be behind some kind of wall or, at least, secured by something more complex than an easily guessable number. Someone at Honda seemingly tried to implement this when they set up a form requiring two out of three: an order number, email address and zipcode. Without that information, the Find My Order page won’t take you to the URL for your order status.
The problem is that the order status page itself had no authentication. Thus, anyone could easily guess order numbers and take data at will. Honda did not appear to use any kind of encoding for the order IDs like other websites. A base 64 encoding might produce something like: “aHR0cHM6Ly93d3cudGhlYXV0b3BpYW4uY29tLw==” as a difficult-to-surmise order ID. Instead, the orders were just a series of five numbers with no letters or special characters.

There are other strategies that can catch slip-ups like these, too. An administrator could set up the server hosting the order status pages with rate limiting. If someone tried to access order statuses too quickly, it would shut off access and raise an alarm to Honda’s personnel. This is a common method that IT security staff use to catch accidental leaks when hackers try to scrape data from a site. It’s not clear whether or not this system is in place, but we were able to query multiple orders.
After receiving the tip, The Autopian worked to verify the leak and the potential affected population. Research revealed orders as early as March this year were accessible on the site, as well as orders made within the last few days. However, the search was non-exhaustive, and customers may be affected outside of those dates. Despite the anonymous tipster finding the leak accidently as they looked into their Motocompacto order, the affected customer base is much wider. Based on the orders we viewed, we estimate thousands to tens of thousands of customers had their details openly posted online. Both completed and canceled orders had details posted on the site, with customers ordering everything from scooters to trim pieces and transmissions.
“It looks like Honda was hoping that obscurity was good enough security, which is unfortunately more common than you’d like to think with e-commerce websites.” said the e-commerce engineer.
If you’re not tech-savvy, here’s what you need to know: Basically, Honda’s site made it easy for anyone to view the names, purchases, partial credit card information, and addresses of customers. Any high-schooler with the ability to write Python could have likely scraped the lot in a few hours, longer if they tried to do so without raising the alarm.
Whether the site has been scraped to harvest all the available data is impossible to know without a detailed inspection of Honda’s server logs. In any case, if you’ve ordered parts from Honda’s Dreamshop site, or if you suspect a dealer has done so for you, there are some precautions you could take. There are basic steps to follow to minimize the chance of malicious actors stealing your identity or compromising your personal accounts.
It bears noting that Honda’s privacy policy, and those of its dealers, essentially cover this exact point. The wording varies depending on the organization. The main one states that Honda employs “reasonable” safeguards to “protect Personal Information from unauthorized access, disclosure, and use.” In this case, that clearly didn’t happen. Regardless, the same old catch-all legal term is there to cover Honda’s backside. “As a result, while we strive to protect information transmitted on or through our Sites or Services, you do so at your own risk.”

If you’ve been affected by this leak, let us know in the comments or via an email to tips@theautopian.com. You can of course remain anonymous.
Additional reporting by Matt Hardigree







You don’t even need the ability to write Python, just get a AI assistant write it for you.
Reminds me of that journalist in Missouri who found SSNs were exposed on a state run website. The journalist reported the issue to the state, not in the news, promising not to reveal the issue until it was already fixed. The state tried to have the journalist arrested for hacking for merely finding the flaw in their system. No charges were ultimately filed, but the accusations and court proceedings put the folks who were trying to merely do the right thing by reporting the problem to the appropriate officials were out thousands of dollars.
That’s a summary, lots more too the actual story.
In case anyone else was curious, the base64 string “aHR0cHM6Ly93d3cudGhlYXV0b3BpYW4uY29tLw==” decodes to “https://www.theautopian.com/”
I don’t know if I’d consider a base64 string to be properly secure in place of a legitimate GUID since it’s reproducible by a well known process. This is just laziness on whoever Honda contracted development of this site out to though.
Yeah, if you’re a tech person reading this please note that base64 encoding something is not remotely secure. If they had done that here all you would need to do is decode the string, increment the order count by 1, and re-encode the new number. Bam, you have the exact same vulnerability.
If you’re relying on an unpredictable ID as your security mechanism you need to use a secure hashing algorithm (ie not something like MD5 either).
There are plenty of non-obvious ways to screw up security in your software, but this one is pretty darn obvious.
“We take the security and privacy of our customers very seriously”
Those words don’t mean what you think they mean….
inconceivable!
This would be a spearphishing goldmine. Crawl the website daily, grab details and send fake “please confirm your order” emails including a request to confirm payment information.
“h0ndacustomersirvace@gmail.com”
“We can talk through telegram to issue the refund”
USPS – The shipment has arrived at the warehouse but cannot be delivered due to incomplete address information
As an IT manager focusing on security and cloud solutions, this is evidence of amateur hour at Honda. I mean, wow. I’ve got car washes and general contractors with more security built into their sites.
So I ordered a Motocompacto from that site last week. I had my order tracking in an open tab that now says that page is under maintenance. There is no new email as of yet from Honda, but clicking on the link in my order routes me to a new page with the info. Luckily I’m not too concerned with this as the card I use is mostly a flow through account that only gets funded when I am making purchases with it.
That all being said: this is not a good look for Honda. This Dream Shop store seems to be the way they would like to operate all parts orders, but if there are security issues like this it seems like a pretty big oversight. Pushing everyone that wants a Motocompacto to order through the non-secure site, hits me in a way that makes me a bit less excited to get the Motocompacto.
“Fret not, consumer. You can still give us money.”
I was the tipster on this one. I was shocked when I discovered this, obviously. Such a shame that a company as big as Honda would screw up this big 🙁
Honda owes me a bug bounty! ????
A free Motocompacto perhaps? Failing that meaningful gesture of appreciation, they could at least send you one of those blue shirts the ‘helpful Honda people’ always wear in those annoying commercials. 🙂
hopefully they don’t just cancel my order now :-p
Edit button, edit button. 🙂
High five to you Sampson! Thanks for being awesome!
haha thanks! Just curious is all. I thought the URL looked way too simple.. seems it was.
This is really sad, Honda tried to throw a bone to enthusiasts and come out with a fun toy you can run around on, but just completely bungled the sales operation, had to deal with uncooperative dealers, and now this. It may teach them the wrong lesson at the end of all of it, but it seems like we used to expect more competence from them than we’ve been seeing lately.
This kind of thing is such a rookie system design mistake. My team exposed s similar thing in a trade show lead scanner system 10 years ago. You’d think people would learn. Apparently not.
The websites they set up for each Honda dealer for online parts order is more secure than this (parts.???honda.com). Strange that they would screw up here.
I’d like to see the slack discussion from this article!
Is it like 2003 or something? Straight URL to SQL has been a No-No for a long time. That is like DB 101. Wow! Obfuscate those parameters. Duh.
Is Honda IT hiring, because I can do that kind of sloppy work too.
Is this Honda or a independent parts supplier? I could not be sure?
FYI The catch all phrases in legal contracts don’t always work. In this case an argument about what reasonable effort is defined as and if the effort was indeed reasonable. I have found many businesses, even large ones will try to save money by copying another contract and adding or deleting their preferred terms whether legal or not. Also many might use their own corporate lawyer instead of a contract lawyer who may not be familiar with contract law.
Whoa. This is entry-level secure-software failure.
https://owasp.org/www-community/attacks/Web_Parameter_Tampering
This kinda stuff was entry-level OWASP stuff over a decade ago. Guessing there’s some SQL injection stuff available too if they’re this careless with the basic stuff.
Do you know if Bobby Tables is available?
So, as long as you know someone’s email address and zip code you can still see all their past orders?
Did you intend to redact both of the order numbers? The first one is blurred; the second is not.
The “partial credit card information” point is a non-issue. The Payment Card Industry Data Security Standard (PCI DSS) allows the last four to be displayed in the clear, because nothing malicious can be done with just the last four. In earlier versions of the DSS (would need to confirm in 4.X), merchants were permitted to display the first six (the Bank ID Number, or BIN) and the last four digits. Each card brand has many BINs. Did you ever notice when you’re entering your credit card info that the web form displays the appropriate card brand logo? It’s basing that on the BIN.
tl;dr – there is/was potential for unauthorized disclosure of Personally Identifiable Information (PII) but this issue does not put financial info at risk. The headline should be modified as this does not expose “Payment Details”.
No, it doesn’t. And I don’t give a damn if you are cranky. That’s a you problem.
Read the article: “Finally, both the credit card type and last four digits of the user’s credit card are also openly visible.”
See that part where it says “last four digits”? That means the last four digits, which is permitted under the DSS. I made no statement about Dreamshop as a whole being/not being PCI compliant, because I don’t know if they are – and neither do you.
You’re probably thinking that because the redacted bits are longer than four characters, they must be the full card number. Guess what? A lot of UIs use asterisks to represent the rest of the digits, so a longer blur means nothing.
Unless you can provide any kind of verifiable info indicating that full card numbers were disclosed, feel free to shut your word hole.
PS It was already clear that this issue affects all the Dreamshop orders because it was covered in the article. Maybe you should read before commenting.
This thread is getting IT spicy!!!
I wouldn’t say that. 🙂
I just get tired of the obnoxious “I KNOW EVERYTHING, THE REST OF YOU KNOW NOTHING, GRAAAAAHH!!” nonsense.
In general this is a very positive environment and most people behave, which is nice.
Yes. “Some commenters” around here are tainting the experience/culture for the rest of us.
I’m with you; it’s getting tiresome.
NERD FIGHT!!!
Honda did not provide full numbers. We checked the pages before redacting them. For card number, it said “Card ending in xxxx” and the numbers are the last four digits.
Thanks, Mercedes!
And I noticed that someone on the team redacted the order number on the second order – much appreciated [thumbsupemoji]
OK, so the CC number issue is a nothing burger. The rest of the issue, though, is bush league fuckery. Good of y’all for reporting this properly.
Yeah, the big issue to me would probably be phishing. There was more than enough information there for a scammer to create a fake Honda website that looked legit enough. Then, taking advantage of the fact that DreamShop is a dumpster fire right now, send out legit-looking emails claiming some payment error or whatever.
My Motocompacto order has been refunded for a second time. However, the dealership swears that DreamShop shouldn’t be taking my money in the first place. Ok, so why did it take $1,080 from me for three days? This whole thing is ripe for a scammer to make some good money.
Maybe they’ll send you 3 scooters.
Ooppsy, my bad
This might end badly for them….
wow, this is like pre-1995 level coding.
If they were collecting payment information, their IT team is entering a shitstorm of auditors from various certification bodies.
If this was available in the EU, even worse.